Wednesday, January 20, 2010
got a large number of folders you want to share on the network?
If you’ve got a large number of folders you want to share on the network, navigating to
each one of them and going into their properties and changing them one by one can be
quite a nuisance. Even sharing can be as simple as “Next, next, and next” with the
Shared Folder Wizard (Start > Run > “shrpubw” > [Enter]).
You can even set share permissions right there, so there’s no need to go back to those
shared folders for additional settings. Just remember to check the “Run this wizard
again” box at the last dialog if you want to move on to the next folder.
What is a Computer worm?
A worm is a program that spreads over a network. Unlike a virus, a worm does not need to attach itself to a host program for propagation. Some worms use email to spread, sending themselves out as an attachment to other users. Some of them exploit the vulnerabilities in software running on a victim’s machine, aiming to take control of those systems. Some worms also spread by using cross-site scripting vulnerabilities in web servers or services.
What is a Trojan?
A Trojan or Trojan horse is a software application that pretends to provide legitimate functionality, but actually carries out malicious functions, exploiting the legitimate authority of the person who starts up the program. It can be used as an attack tool to capture sensitive information such as user accounts and passwords. Unlike a virus, a Trojan does not replicate itself. It spreads usually by enticing the user to install software such as “shareware” which is embedded with a Trojan horse.
What is spyware?
Spyware is a type of software that secretly forwards information about a user's online activities to third parties without the user's knowledge or permission. The information is mainly used for purposes related to advertising. For example, sending spam emails to the user in order to deliver targeted advertisements by marketers. Some spyware might also be able to steal a victim’s files or even keystrokes to gain sensitive and personal information.
What is adware?
Adware is a type of software that displays advertising banners while a program is running. Most adware is also spyware. In many cases, freeware developers offer their products free-of-charge to users, receiving financial support from adware marketers by bundling adware into freeware products.
You should carefully read the terms of use before installing any freeware or shareware. The use of freeware and shareware may sometimes imply that you agreed to install adware systems as well.
What are backdoor programs?
Backdoor is a general term for a malicious program that listens for commands on a certain network port. Most backdoors consist of a client component and a server component. The client component resides on the attacker's remote computer, and the server part resides on the infected system. When a connection between client and server is established, the remote attacker has a degree of control over the infected computer. For example, a backdoor may allow a attacker to monitor or take control of an infected computer, stealing data from it, uploading and activating viruses, or erasing user data and so on.
FIND YOUR LOST MOBILE WITHOUT GOING TO POLICE STATION

IMEI NUMBER WILL HEPL YOU TO FIND YOUR LOST MOBILE
WHAT IS IMEI ?
An IMEI numberis The International Mobile Equipment Identity (IMEI) number it is an international identity number used to uniquely identify a mobile phone.
The 15-digit IMEI number is an electronic fingerprint transmitted every time a phone is used,
which reveals the identity of the mobile handset.
CREATE YOUR OWN MOBILE THEMES
KEYBOARD SHORTCUTS FOR UBUNTU
General keyboard shortcuts
- Ctrl + A = Select all
- Ctrl + C = Copy the highlighted content to clipboard
- Ctrl + V = Paste the clipboard content
- Ctrl + N = New (Create a new document, not in terminal)
- Ctrl + O = Open a document
- Ctrl + S = Save the current document
- Ctrl + P = Print the current document
- Ctrl + W = Close the close document
- Ctrl + Q = Quit the current application
Send Free SMS Without Any Ads Using Yahoo Mail
It is very easy to send free sms without any advertisements using yahoo mail’s inbuilt chat system. Following is the detailed tutorial on sending ad free sms using yahoo mail -
1. Log into yahoo mail. Then sign into the yahoo mail in built chat feature. To do this, click on the status message (It is next to your welcome message, say, Hi Chris) on the top left part of the yahoo mail interface and choose Available.
2. Click on New -> Text Message(SMS) or simply press t, to open the conversation tab.
3. Type the mobile number of your friend in the the text box. Yahoo will automatically start suggesting the number if it is already added in your contacts, like this,
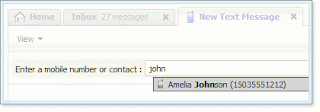 If it doesn’t suggests anything then it means that the number is not in your contacts. But it doesn’t matter if the receiver is in your contacts or not. Just type the phone number and message, and click on send. Your sms will be sent immediately.
If it doesn’t suggests anything then it means that the number is not in your contacts. But it doesn’t matter if the receiver is in your contacts or not. Just type the phone number and message, and click on send. Your sms will be sent immediately.
Note 1 - Don’t forget to include the area code while typing the phone number.
Note 2 - The maximum length for a sms is 158 characters which includes spaces as well. It is actually a short messaging service.
Note 3 - This feature is free but you can send maximum five messages to a person until he replies. The quota for the five messages starts again once the contact replies you. The replies will be available in the conversation area, like this,
Note 4 - The pricing of replying to a message depends on your mobile service provider.
Note 5 - At the time of writing, this service is available only in India, Philippines, Canada, India, Indonesia, Vietnam, U.S. and Malaysia.
Note 6 - In India, the following operators are supported,
1. Log into yahoo mail. Then sign into the yahoo mail in built chat feature. To do this, click on the status message (It is next to your welcome message, say, Hi Chris) on the top left part of the yahoo mail interface and choose Available.
2. Click on New -> Text Message(SMS) or simply press t, to open the conversation tab.
3. Type the mobile number of your friend in the the text box. Yahoo will automatically start suggesting the number if it is already added in your contacts, like this,
 If it doesn’t suggests anything then it means that the number is not in your contacts. But it doesn’t matter if the receiver is in your contacts or not. Just type the phone number and message, and click on send. Your sms will be sent immediately.
If it doesn’t suggests anything then it means that the number is not in your contacts. But it doesn’t matter if the receiver is in your contacts or not. Just type the phone number and message, and click on send. Your sms will be sent immediately.Note 1 - Don’t forget to include the area code while typing the phone number.
Note 2 - The maximum length for a sms is 158 characters which includes spaces as well. It is actually a short messaging service.
Note 3 - This feature is free but you can send maximum five messages to a person until he replies. The quota for the five messages starts again once the contact replies you. The replies will be available in the conversation area, like this,
Note 4 - The pricing of replying to a message depends on your mobile service provider.
Note 5 - At the time of writing, this service is available only in India, Philippines, Canada, India, Indonesia, Vietnam, U.S. and Malaysia.
Note 6 - In India, the following operators are supported,
- Airtel
- Hutch
- Reliance CDMA
- Reliance GSM
- Tata
- Spice
- Idea
- MTNL
- Aircel
- BPL
Chat with Friends through ms dos Command Prompt
1) All you need is your friend's IP Address and your Command Prompt.
2) Open Notepad and write this code as it is.....!
Use pen drive as ram
Now a days we can use pen drive itself as a RAM for our system and just increase the general boot up speed and also operational speed of the system . Now a question arises that "Is it possible only for those who have Vista OS " ? my answer is a Big NOOOO..
Why is it that Anti-Virus software cannot repair files that are infected by a Trojan or a worm?
Strictly speaking, there is no such thing as “file infected by a Trojan or a worm”. One difference between a virus and a Trojan or a worm is that a virus will replicate itself to a clean file, which will in turn infect other clean files when the infected file is executed or opened.
A Trojan is a malicious program installed on an infected computer which does not attach itself to any file. Worms are also malicious software that spread across networks but do not replicate onto a clean file. Therefore, there is no file to repair when it comes to a Trojan or a worm.
A Trojan is a malicious program installed on an infected computer which does not attach itself to any file. Worms are also malicious software that spread across networks but do not replicate onto a clean file. Therefore, there is no file to repair when it comes to a Trojan or a worm.
How can I protect my PC against viruses and malicious code?
 Always install and enable anti-virus software or malicious code detection and repair tools. You can also consider similar products that work against spyware and adware. You should enable and configure the live update feature of your virus signature and malicious code definition files, if available, setting the frequency to update daily. If automatic update is not possible, manual updates should be conducted at least once a week.
Always install and enable anti-virus software or malicious code detection and repair tools. You can also consider similar products that work against spyware and adware. You should enable and configure the live update feature of your virus signature and malicious code definition files, if available, setting the frequency to update daily. If automatic update is not possible, manual updates should be conducted at least once a week.What should I do if I receive virus-infected emails generated by mass-mailing viruses?

You should reject and delete such virus-infected emails and never open any attachment in such messages. You should also ensure that you have adequate virus protection measures in place on your computers, and that anti-virus software is kept up to date with the latest virus signatures and detection and repair engines. Unless it is possible to verify the apparent sender address of the virus-infected email, do not send any enquiry message to the apparent sender because in most of the cases, the sender address is spoofed and the sender whose email address it is has nothing to do with the virus-infected message. This avoids further confusion and unnecessary allegations.
Disable Automatic Windows Update
Windows XP is configured out of the box to routinely scan for and download updates to Windows XP automatically. While this can be somewhat convenient for those with very fast Internet connections and those who would otherwise forget to check for updates, it can be a nuisance for the rest of us, who are still using 56k or, even worse 33k modem connections.
Increase Hard Disk speed in Windows

If you like to increase/optimize your Hard Disk I/O - read/write speed without buying expensive software utilities to do that job or changing the HD, just follow next steps. With doing these steps you will increase Hard disk speed (depends of manufacture and specification, but its worth to try). The most speed improvement is visible with IDE drives; however there are reports that this tweak also does good for SCSI disks.
Open Unknown File Types
“I have a strange icon on my desktop. How do I open the file I just downloaded?” I am sure you heard something similar to this at least a few times, or maybe you asked yourselves about opening some file with a strange extension. Of course, you can easily use Google to search for details about the tools needed to open .ISO or .7Z files, for example, but why not have a program do that for you, and then some?
Most power users will laugh at this, but no matter how trivial may seem to be, using the OpenWith.org desktop tool can help you save a lot of your precious time, and since this is the most important asset one has, right after health and freedom… I didn’t pick this subject just to post another article here! When you need to open unknown file types, everything gets much easier if the research part is already done, there’s no need to argue about that.
Most power users will laugh at this, but no matter how trivial may seem to be, using the OpenWith.org desktop tool can help you save a lot of your precious time, and since this is the most important asset one has, right after health and freedom… I didn’t pick this subject just to post another article here! When you need to open unknown file types, everything gets much easier if the research part is already done, there’s no need to argue about that.
Tuesday, January 19, 2010
Learn programming of batch file
Who should read this Book?
This book is for everybody from a Beginner to a Geek. Anybody who wants to become a Hacker then this is a what you need to know before even thinking to become a Hacker.
What can you get from it?
This book contains everything about Batch File Programing from beginning to the end. I will list out the table of content of the E-book.
· Introduction
· Internal & External Commands
· Run Line Commands
· Batch Operators
· Basic Commands
· Environment Variables
· Looping Statements
· Conditional Statements
· Commands Associated with files and folders
· Network Troubleshooting commands
· Code snippets
· Virus Programming
· Converting Batch to Executable
I know all of you are thinking about the second-last topic in the list. Yes it is about virus programing and it true that you can make your own viruses using Batch Programming. This is an Exhaustive guide from which you can get all the thing that you need to know about Batch Programming.
Where can I get this E-Book?
Note: after download use password:- youthicon.info
Delete administrator Password without any software
Boot up with DOS and delete the sam.exe and sam.log files from Windows\system32\config in your hard drive. Now when you boot up in NT the password on your built-in administrator account will be blank (No password). This solution works only if your hard drive is FAT.
OR
1. Put your hard disk of your computer in any other pc .
2. Boot that computer and use your hard disk as a secondary hard disk(i.e. don’t boot as primary hard disk ).
3. Then open that drive in which the victim’s window(or your window) is installed.
4. Go to location windows->system32->config
5. And delete SAM.exe and SAM.log file
6. done!!
7. Now remove victim’s hard disk(your hard disk) and put in your computer.
8. And boot your computer:-)
Recover Windows Passwords
If you are stranded in a situation where you either don’t remember the password to your Windows account or are trying to help a Windows user by logging to a machine whose user has forgotten the password, this post will be of help to you.
Ophcrack is a free Windows password cracker based on rainbow tables. It is a very efficient implementation of rainbow tables done by the inventors of the method. It comes with a Graphical User Interface and runs on multiple platforms.
Follow the steps below to recover Windows user id and password information
1.) Point your browser to http://ophcrack.sourceforge.net/ and download ophcrack live cd image for your OS depending on whether you run Windows XP or Vista.
Download ophcrack live-cd for Windows XP or Windows Vista
2.) Once you have downloaded the image, you can write this image into a cd or dvd for use.
3.) Insert the DVD with the live cd image and reboot your computer. Ensure that you make CD Drive as the primary boot device. The computer should now boot using the Live CD you burnt on the DVD earlier.
4.) Select the first mode which says ” ophcrack graphic mode” and hit Enter.
5.) Upon hitting enter, the software will take you to a user interface and will begin scanning for the userid’s and passwords.
ophcrack gives you the list of userid and password combinations after completing the scan.
6.) Once you have the userid and password, you can remove the CD and login again to the Windows terminal using the userid and password obtained.
Rapidshare downloader
Rapidshare allows to download only a single file at a time with free account. If you want to download multiple files at the same time, you need to buy a premium account but now you can download multiple files from Rapidshare free account without paying anything with RapidShare Download Accelerator
Note: after download use password:- youthicon.info
With RapidShare Download Accelerator, you can add all the files you'd like to download, and it will do all the annoying work for you. Now you can just sit back and watch your files download without paying a dime.
Ever had to download multiple free files from RapidShare only to realize they make it nearly impossible unless you have a paid account. With RapidShare Download Accelerator, you can add all the files you'd like to download, and it will do all the annoying work for you. Now you can just sit back and watch your files download without paying a dime.
.NET Framework is required to run this program.
Hack Mobile Phone by using bluetooth
This is the mobile app which allows you to gain access to one's phone via bluetooth without their knowledge,using bluetooth hacking software u can hack any mobile or cell phones this software is the latest version Bluetooth Hack v 1.07. click here to download.
Note: after download use password: youthicon.info
Advantages of this software:
Once if ur connected to another phone via bluetooth you can:
- u can read his/her messagess
- u can read his/her contactss
- u can change hi/her profile
- u can also play his/her ringtones even his/her phone is in silent
- u can play his songs from his/her mobile
- u can restart his/her mobile
- u can switch off his/her mobile
- u can restore his/her factory setings
- u can also change ringing volume of his/her mobile..
- the best part of it is u can call from his mobile which also includes all call functions like hold on etc etc...
This software is very much suitable for sony ericcsson mobiles.
enjoy!!
- u can read his/her messagess
- u can read his/her contactss
- u can change hi/her profile
- u can also play his/her ringtones even his/her phone is in silent
- u can play his songs from his/her mobile
- u can restart his/her mobile
- u can switch off his/her mobile
- u can restore his/her factory setings
- u can also change ringing volume of his/her mobile..
- the best part of it is u can call from his mobile which also includes all call functions like hold on etc etc...
This software is very much suitable for sony ericcsson mobiles.
enjoy!!
Subscribe to:
Posts (Atom)